- Meraki Client VPN uses the Password Authentication Protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption. User credentials are never transmitted in clear text over the WAN or the LAN.
- Make network security safer and easier with the Cisco Meraki MX64 firewall. The Meraki MX64 firewall is 100% cloud managed and has a simple deployment.
Considerations for VPN Firewall Rules
When configuring VPN Firewall rules, it is important to remember that traffic should be stopped as close to the originating client device as possible. This cuts down on traffic over the VPN tunnel and will result in the best network performance. Because of this, site-to-site firewall rules are applied only to outgoing traffic. As such, the MX cannot block VPN traffic initiated by non-Meraki peers.
Who you buy Cisco Meraki from matters. That is why we offer the option of Managed Services with each Cisco Meraki purchase. Our goal at Firewalls.com is to be your go to Cisco Meraki store and your MX firewall managed service provider so give us a call and see the difference that we can bring to your business. In this example, we will be setting up a connection from a Palo Alto firewall with an external IP addresses of 1.2.3.4 and a Cisco Meraki MX64 firewall with an external IP address of 6.7.8.9. Yes, those aren’t the real IP addresses I’m using, but other than the obfuscation of the actual source and destination IP addresses of the tunnel. Meraki Client VPN uses the Password Authentication Protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption.
The image below demonstrates a misconfigured site-to-site firewall rule. Site-to-site firewall rules only apply to outbound traffic. This rule will never be applied as the source subnet is not a LAN subnet on the MX:
Meraki Firewall Vpn Configuration
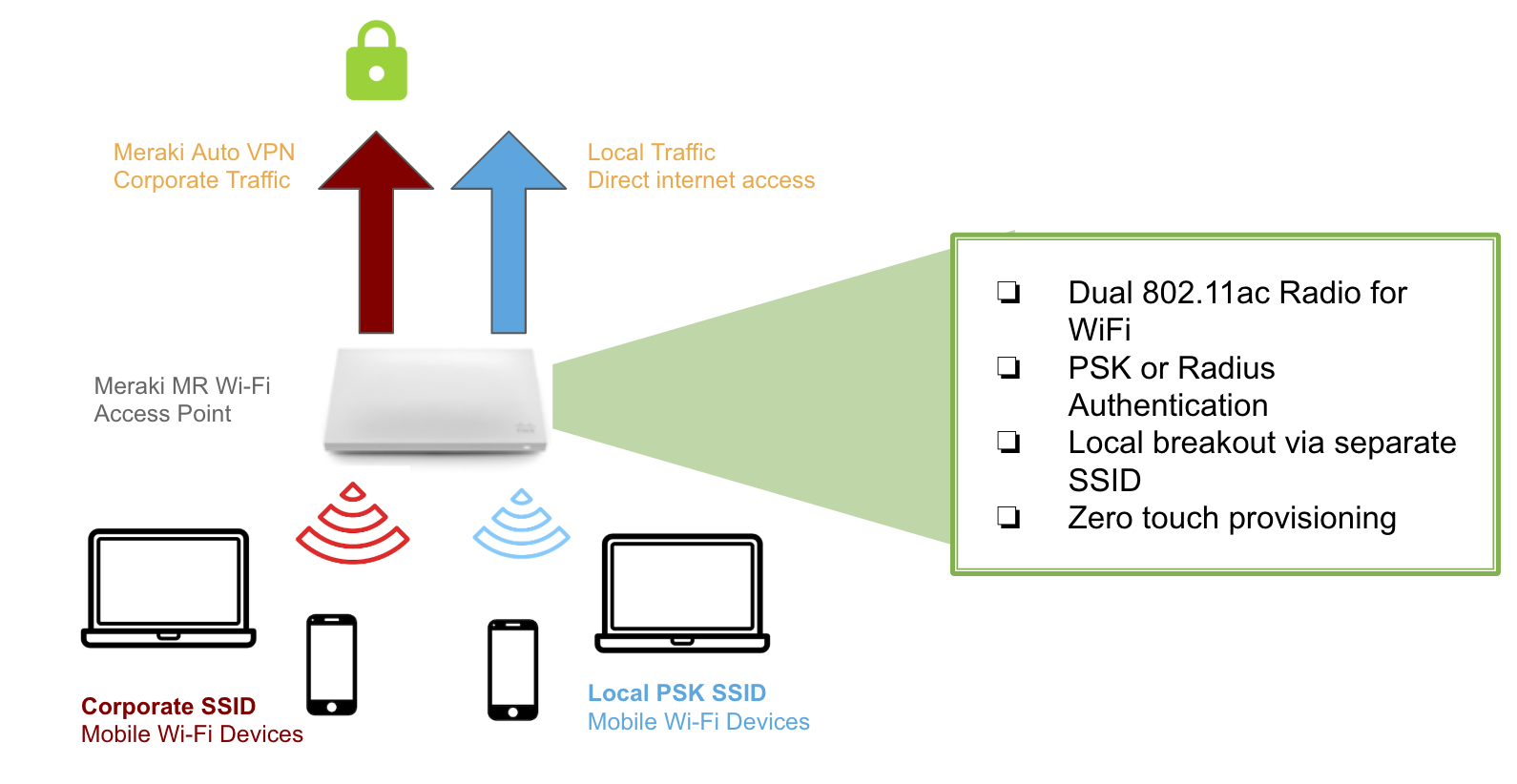
Meraki Mx64 Client Vpn Setup

The following image demonstrates a site to site firewall rule that will be applied correctly. Traffic from the 10.0.1.0/24 subnet will not be able to reach 10.0.2.0/24 subnet since the 10.0.1.0/24 subnet is a LAN subnet on the MX.
When traffic passing through the MX matches a site-to-site VPN route, VPN firewall rules are applied in descending order. VPN traffic to both AutoVPN and Non-Meraki peers is only subject to the site-to-site firewall rules and is never subject to global Layer 3 firewall rules.
