Open Start Menu - Search “VPN” - Click Change virtual private networks (VPN). From the VPN settings page, click Add a VPN connection.3 3. In the Add a VPN connection dialog: Set the VPN provider to Windows (built-in) Provide a Connection name for the VPN connection. Specify a public IP address (found in Dashboard, under Security appliance - Monitor. Do you want access to your resources remotely?- Do your employees work outside of the office?- Do you want RDP to servers from anywhere?. When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud. Usernames are generated based on a hash of a unique identifier on the device and the username of that device. Cisco Meraki uses the integrated Windows client for VPN connection (no Cisco client at this time). To be able to connect with simple AD user account credentials, along with.
This page provides instructions for configuring client VPN services through the Dashboard.
For detailed instructions on how to configure a client VPN connection on various client device platforms, please refer to:
Client VPN
The client VPN service uses the L2TP tunneling protocol and can be deployed without any additional software on PCs, Macs, iOS devices, and Android devices, since all of these operating systems natively support L2TP VPN connections.
Note: TLS (SSL) Client VPN is supported on the MX with AnyConnect. To learn more, see AnyConnect on the MX
Note: Linux-based operating systems can support client VPN connections as well, although third-party packages may be necessary to support L2TP/IP.
Note: Establishing a client VPN connection when the client is located on the LAN of the MX is unsupported.
Encryption Method
Client VPN uses the L2TP/IP protocol, with the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase2. As a best practice, the shared secret should not contain any special characters at the beginning or end.

Owing to changes in the PCI-DSS Standard version 3.2.1, some auditors are now enforcing requirements for stronger encryption than the Meraki Client VPN default settings provide. Please contact Meraki Support if you need these values adjusted, but please be aware that some client devices may not support these more stringent requirements (AES128 encryption with DH group 14 - Required by PCI-DSS 3.2.1).
Client VPN Server Settings
To enable Client VPN, choose Enabled from the Client VPN server pulldown menu on the Security Appliance > Configure > Client VPN page. The following Client VPN options can be configured:
- Client VPN Subnet: The subnet that will be used for Client VPN connections. This should be a private subnet that is not in use anywhere else in the network. The MX will be the default gateway on this subnet and will route traffic to and from this subnet.
- Hostname: This is the hostname of the MX that Client VPN users will use to connect. This hostname is a DDNS host record correlating to the Public IP address of the MX. You can change this hostname by following the instructions here.
- DNS server: The servers VPN Clients will use to resolve DNS hostnames. Chose from Google Public DNS, OpenDNS, or specifying custom DNS servers by IP address.
- WINS server: If VPN clients should use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
- Shared secret: The shared secret that will be used to establish the Client VPN connection.
- Authentication: How VPN Clients will be authenticated (see below).
- Systems Manager Sentry VPN security: Configuration settings for whether devices enrolled in systems manager should receive a configuration to connect to the Client VPN (see below Systems Manager Sentry VPN Security section).
Authentication
Meraki Client VPN uses the Password Authentication Protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption. User credentials are never transmitted in clear text over the WAN or the LAN. An attacker sniffing on the network will never see user credentials because PAP is the inner authentication mechanism used inside the encrypted IPsec tunnel.
The authentication itself can be performed by using these three options: the Meraki cloud, RADIUS, or Active Directory. Below, the three options are discussed.
Meraki Cloud Authentication
Use this option if an Active Directory or RADIUS server is not available, or if VPN users should be managed via the Meraki cloud. To add or remove users, use the User Management section at the bottom of the page. Add a user by clicking 'Add new user' and entering the following information:
- Name: Enter the user's name.
- Email: Enter the user's email address.
- Password: Enter a password for the user or click 'Generate' to automatically generate a password.
- Authorized: Select whether this user is authorized to use the Client VPN.
To edit an existing user, click on the user under the User Management section. To delete a user, click the X next to the user on the right side of the user list.
When using Meraki hosted authentication, the user's email address is the username that is used for authentication.
RADIUS
Use this option to authenticate users on a RADIUS server. Click Add a RADIUS server to configure the server(s) to use. Enter in the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.
For more information on how to configure Radius authentication for Client VPN, refer to the documentation on Configuring RADIUS Authentication with Client VPN.
Note: If multiple RADIUS servers are configured, RADIUS traffic will not be load balanced.
Active Directory
Use this option if user authentication should be done with Active Directory domain credentials. You will need to provide the following information:
- Short domain: The short name of the Active Directory domain.
- Server IP: The IP address of an Active Directory server on the MX LAN or a remote subnet routable through AutoVPN.
- Domain admin: The domain administrator account the MX should use to query the server.
- Password: Password for the domain administrator account.
For example, considering the following scenario: Users in the domain test.company.com should be authenticated using an Active Directory server with IP 172.16.1.10. Users normally log into the domain using the format 'test/username' and you have created a domain administrator account with the username 'vpnadmin' and the password 'vpnpassword'.
- The Short domain would be 'test'.
- The Server IP would be 172.16.1.10.
- The Domain admin would be 'vpnadmin'.
- The Password would be 'vpnpassword'.
Refer to the Active Directory documentation for more information about integrating AD with Client VPN.
Note: At this time, the MX does not support mapping group policies via Active Directory for users connecting through the Client VPN.
Systems Manager Sentry VPN Security
When using Meraki cloud authentication, Systems Manager Sentry VPN security can be configured If your Dashboard organization contains one or more MDM networks. Systems Manager Sentry VPN security allows for devices enrolled in Systems Manager to receive the configuration to connect to the Client VPN through the Systems Manager profile on the device.
To enable Systems Manager Sentry VPN security, choose Enabled from the Client VPN server pulldown menu on the Security Appliance > Configure > Client VPN page. You can configure the following options:
- Install Scope: The install scope allows for a selection of Systems Manager tags for a particular MDM network. Devices with these tags applied in a Systems Manager network will receive a configuration to connect to this network's Client VPN server through their Systems Manager profile.
- Send All Traffic: Select whether all client traffic should be sent to the MX.
- Proxy: Whether a proxy should be used for this VPN connection. This can be set to automatic, manual, or disabled
When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud.
Usernames are generated based on a hash of a unique identifier on the device and the username of that device. Passwords are randomly generated.
Client VPN Connections
After configuring Client VPN and users are starting to connect, it may be useful to see how many and what client devices are connected to your network via Client VPN. To see connected Client VPN devices, navigate to Network-wide > Clients > click the dropdown icon on the Search clients... search bar > make sure to select Client VPN and either Online, Offline or both.
Group Policies
It is possible to manually apply group policies to clients connected via Client VPN. Group Policy applied to a client VPN user is associated with the username and not the device. Different devices that connect to Client VPN with the same username will receive the same group policy. For more help on assigning or removing group policies applied to a client, refer to the Creating and Applying Group Policies document.
Note: It is not possible to assign group policies automatically once a user connects to Client VPN.
FAQs Page
If further guidance is required, please feel free to visit the FAQs page built into Client VPN page (Security Appliance > Configure > Client VPN > FAQs). The FAQs contain answers and links (KB Articles and Dashboard pages) to the most common Client VPN inquiries. Below is a snippet of the FAQs page.
This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our Client VPN Overviewdocumentation.
For troubleshooting, please refer to our Troubleshooting Client VPN documentation.
Android
To configure an Android device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> Wireless & Networks -> VPN
- Click the Plus Icon to add an additional VPN profile
Name: This can be anything you want to name this connection, for example, 'Work VPN.'
Type: select L2TP/IPSEC PSK
Server address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
IPSec pre-shared key: Enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Press save
You will be prompted for user credentials when you connect.
Chrome OS
Chrome OS based devices can be configured to connect to the Client VPN feature on MX Security Appliances. This allows remote users to securely connect to the LAN. This article will cover how to configure the VPN connection on a Chrome OS device. For more information on how to setup the Client VPN feature of the MX or how to connect from other operating systems, please visit the MX documentation.
- If you haven't already, sign in to your Chromebook.
- Click the status area at the bottom of your screen, where your account picture is located.
- Select Settings.
- In the 'Internet connection' section, click Add connection.
- Select Add private network.
- In the box that appears, fill in the information below:
- Server hostname:Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Service name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Provider type: Select L2TP/IPsec + Pre-shared key.
- Pre-shared key: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Username credentials for connecting to VPN. If using Meraki authentication, this will be an e-mail address.
- Password credentials for connecting to VPN.
- Click Connect.
For more information regarding the configuration of VPN connections in Chrome OS, visit the Google Support page.
To configure an iOS device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> General-> VPN -> Add VPN Configuration...
- Type: set to L2TP.
- Description:This can be anything you want to name this connection, for example, 'Work VPN.'
- Server: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account: Enter the username
- Password: Enter if desired. If the password is left blank, it will need to be entered each time the device attempts to connect to the Client VPN.
- Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Ensure that Send All Traffic is set to On.
- Save the configuration.
macOS
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).

When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
The instructions below are tested on Mac OS 10.7.3 (Lion).
Open System Preferences > Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Server Address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account Name: Enter the account name of the user (based on AD, RADIUS or Meraki Cloud authentication).
- User Authentication > Password: User password (based on AD, RADIUS or Meraki Cloud authentication).
- Machine Authentication > Shared Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
The VPN connectivity will not be established if you don't enable the Send all traffic over VPN connection option!
Windows 7
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Control Panel, click on Network and Internet, click on View network status and tasks.
In the Set up a connection or network pop-up window, choose Connect to a workplace (Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Choose 'Don't connect now; just set it up so that I can connect later' option.
Click Next. In the next dialog window, enter the user credentials, and click Create.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 8
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Network and Sharing Center and click Settings.
In the Set Up a Connection or Network pop-up window, choose Connect to a workplace.
(Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a Workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Go back to Network and Sharing Center and click Change Adapter Settings.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 10
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Search 'VPN' > Click Change virtual private networks (VPN)
From the VPN settings page, click Add a VPN connection.
In the Add a VPN connection dialog:
- VPN provider: Set to Windows (built-in)
- Connection name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Server name or address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- VPN type: Select L2TP/IPsec with pre-shared key
- User name and Password: optional
Press Save.
After the VPN connection has been created, click Change adapter options under Related settings.

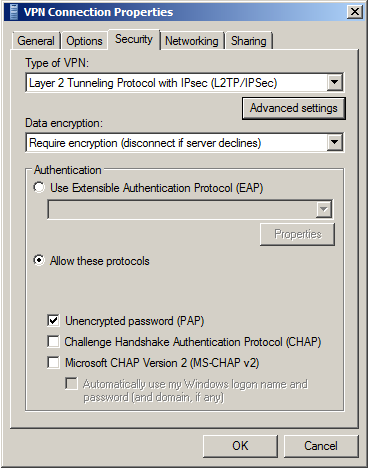
Right-click on the VPN Connection from the list of adapters and click Properties.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
In Advanced Properties dialog box, choose 'Use preshared key for authentication' and enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.
Find your VPN profile and click Connect.
Windows XP
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, use the email address for VPN account / user name.
Open Start Menu > Control Panel, click on Network Connections.
In the Network Tasks section, click on Create a new connection.
Choose Connect to the network at my workplace, in the New Connection Wizard window.
Choose Virtual Private Network connection in the next section.
Then, give a name for this connection. This can be anything you want to name this connection, for example, 'Work VPN.'
Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
In the Connect <Connection Name> box, click on Properties
In the General tab, verify the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Since Client VPN uses the L2TP over IPsec standard, any Linux client that properly supports this standard should suffice. Please note that newer versions of Ubuntu do not ship with a VPN client that supports L2TP/IP, and will therefore require a 3rd party VPN client that supports the protocol.
Note: The xl2tp package does not send user credentials properly to the MX when using Meraki Cloud Controller authentication, and this causes the authentication request to fail. Active Directory or RADIUS authentication can be used instead for successful authentication.
Configuring Ubuntu 20.04
Ubuntu does not support L2TP VPN by default. You will need to install a couple of software packages to enable this functionality. The instructions below were written for Ubuntu 20.04 LTS with the Gnome desktop environment. Ubuntu versions 16.04 and 18.04 can be configured in a similar manner. However, due to the large number of Linux versions available, it is not feasible to document every supported Ubuntu version.
In order to begin the VPN setup, open up a terminal window. Do this by searching for Terminal in your application list. Click on the Terminal icon to open a new terminal session.
Once the terminal window appears, you will need to enter a few commands.
Note: You will need to be a part of the “sudoers” group to install these packages. If you receive an error message like “<username> is not in the sudoers file.” you will need to either adjust your permissions, contact your administrator to add your account as an administrator or have them install the software for you.
Once the packages have been installed, you may open up the Network Settings by searching for Settings in the application list, or by clicking on the Network icon at the top right of the screen and selecting Wired (or Wireless) Settings.
Once the Network Settings window pops up, you will see there is a VPN section listed. Click on the + icon to set up a new VPN connection.
Select the Layer 2 Tunneling Protocol (L2TP) VPN type on the modal pop up window. If L2TP is not listed as an option, please see the first step about installing the required packages.
After selecting the L2TP option, a new modal will pop up titled Add VPN. Fill out your VPN Name, Gateway, User name, and Password information here.
Note: To save your password on this screen, you must select the appropriate option from the question mark on the password field.
Next, click on the IPsec Settings button to open the L2TP IPsec Options modal.
Once the modal pops up, expand the Advanced options, and enter the following:
Select OK to continue. You will be returned back to the Add VPN modal. Select the PPP Settings button.
On the L2TP PPP Options modal, select only the PAP authentication method. Be sure the other authentication methods are de-selected. All other options can remain as the default. Select OK to continue.
Select Add at the top right corner of the Add VPN modal to complete the VPN setup.
Now you may connect your VPN by toggling the button on the Network Settings page:
Or by selecting the Connect option from the top right corner menu.
Upon successful connection, a VPN icon will appear next to the network icon in the status bar.
Configure Meraki Vpn Radius
Note: The version of network-manager-l2tp that is installed along with xl2tpd is known to cause issues when connecting to Meraki Appliances. To alleviate this, you must disable the xl2tpd service when using the network-manager GUI to connect to a Meraki VPN.
To stop the xl2tpd service once use this Terminal command:
sudo service xl2tpd stop
To stop the xl2tpd service for all subsequent reboots use this Terminal command:
Setup Meraki Vpn To Azure
sudo update-rc.d xl2tpd disable
